In this post, I have summarized how I have performed a password recovery of a WordPress installation. I have followed the instructions here. I have performed a WordPress password reset via database (Step 1 through 6) as well as a WordPress password reset via WP CLI (Appendix).
Note: This document shows even more options on how to perform a WordPress password reset.
Shoot! After importing a full WordPress backup made on WordPress.com into a new test WordPress installation on OpenShift, I could not log in to the test installation anymore. I do not know, why, but neither the password I have used on the target system nor the password used on the source system has worked. It is Password Reset Time!
Step 1: Log in to Database System
I am running my new WordPress test site on OpenShift. The next few commands are used to log into the database container of the WordPress installation.
oc login
oc project wordpress # please adapt!
POD=pod/$(oc get pods | grep Running | grep '\-db\-' | awk '{print $1}'); echo $POD
oc rsh $PODIf your Database is running on a native machine (physical or virtual), just SSH into the system.
ssh [-i <path-to-your-ssh-key>] <youruser>@<your-db-system>
Step 2: Start SQL Client
On the container, we start the interactive MySQL client shell:
mysql -u $MYSQL_USER --password=$MYSQL_PASSWORD $MYSQL_DATABASE
Step 3 (optional): Get Overview about Users
Then:
mysql> SELECT ID, user_login, user_pass FROM wp_users; +----+----------------+------------------------------------+ | ID | user_login | user_pass | +----+----------------+------------------------------------+ | ... | | 5 | oveits | $P$BW3e9346724589545679935UHb7v1O/ | | ... | +----+----------------+------------------------------------+ 7 rows in set (0.00 sec)
Step 4: Create a temporary Password Hash
Use some temporary password and hash it here: http://tools.k2an.com/?page=wordpress 
Why temporary password? You sure do not trust the Internet, so it is better to either use a local password hash generator, or you can use an online tool to create the hash of a temporary password you will change later on. I have used the second option.
Step 5: Update the Password Hash in the Database
If the Database is not running on Docker, you might need to set the following variables appropriately. This is not needed on Docker-based installations (also: Kubernetes, OpenShift) since the Docker container is started with those variables set already:
MYSQL_USER=mysql-user MYSQL_PASSWORD=mysql_password MYSQL_DATABASE=wordpress
Now we can update the value as follows: use your User and Password hash in the following command run on the Linux Shell of the Database server (not in the MySQL shell):
USER=oveits PASS='$P$BW3efLpF384965t89erzqS2ul5UHb7v1O/' echo $USER echo $PASS
Do not forget to encapsulate the password into single quotes. This is needed, so $P and $BW… is not replaced by empty values. Check the output of the echo commands.
Then we run following command on the Linux shell:
mysql -u $MYSQL_USER --password=$MYSQL_PASSWORD $MYSQL_DATABASE -e "update wp_users set user_pass=\"$PASS\" WHERE user_login = \"$USER\";"
Running it on the Linux shell helps us using the USER and PASS variables defined before.
Step 6: Log in and change the password
Now is the time to log in with the temporary password:
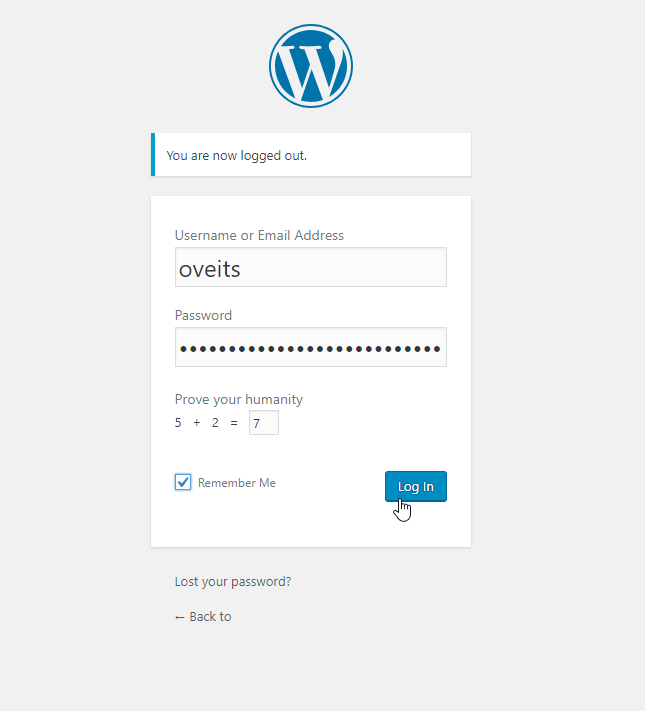
Now, we can change the password on the upper right profile icon.
or, of the source installation was WordPress.com, it will look like follows:
Appendix A: Password Problems with Imports from WordPress.com
In my case, the source of the backup is located on WordPress.com. The import of the backup from a WordPress.com installation seems to keep a connection between your local installation and the WordPress user database. At least, when you click on the profile on the upper right, and then „Security“, you are directed to wordpress.com.
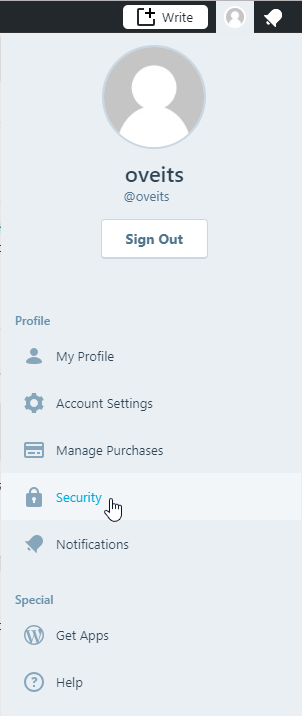
Since the target machine is a local installation, changing the password on WordPress.com has no effect on the local installation. We still need to reset the local password, and the Profile -> Security way of resetting the password does not help.
The correct solution would be to figure out, how to get rid of the redirection to WordPress.com. A quick&dirty way of solving the problem is to access the local profile directly:
https://<your-wordpress-server>/wp-admin/profile.php
You just append „/profile.php“ on the wp-admin link and you reach the local profile, where you can reset the password as described in step 6 above.
Appendix: Password Reset via WP CLI
My WordPress Installation is running on OpenShift/Kubernetes/Docker, so I am using the Docker way of running WP-CLI on the OpenShift node the WordPress Container is running on.
# find the POD
oc login
oc project wordpress
POD=$(oc get pods | grep Running | grep -v '\-db\-' | awk '{print $1}')
echo $POD
# find the container
docker ps
CONTAINER=$(docker ps | grep $POD | grep -v k8s_POD | awk '{print $1}')
echo $CONTAINER
# run a docker command with same volumes and network:
alias wp="docker run -it --rm --volumes-from $CONTAINER --network container:$CONTAINER wordpress:cli --path=/opt/app-root/src $@"
wp user listThe last command will give an output like
# alias wp="docker run -it --rm --volumes-from $CONTAINER --network container:$CONTAINER wordpress:cli --path=/opt/app-root/src $@" # wp user list +----+----------------+----------------+---------------------------+---------------------+---------------+ | ID | user_login | display_name | user_email | user_registered | roles | +----+----------------+----------------+---------------------------+---------------------+---------------+ ... | 5 | youruser | youruser | ... | administrator | ... +----+----------------+----------------+---------------------------+---------------------+---------------+
Assuming that the alias is created appropriately, we now can reset the password via (change ID 5 and password to match your needs):
# wp user update 5 --user_pass='$UP3RstrongP4$$w0rd'
sendmail: can't connect to remote host (127.0.0.1): Connection refused
Success: Updated user 5.
You can safely ignore the sendmail error.